
Workday Authorisation and Authentication
As businesses grow, managing employee data becomes increasingly complex. The security of sensitive employee data is essential, and companies must take steps to ensure that it remains safe from unauthorized access. Workday is a cloud-based software platform that offers HR, finance, and accounting solutions to businesses. In this blog, we will explore Workday security, its features, and best practices to secure employee data.
Workday Security Overview:
Workday provides a range of security features designed to safeguard employee data. These features include:
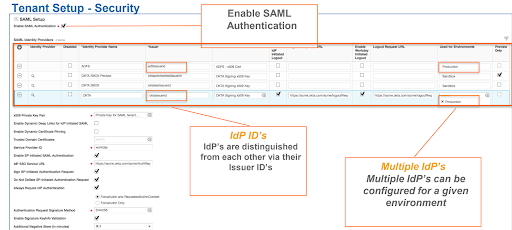
1. Authentication and Authorization: Workday uses multi-factor authentication (MFA) and single sign-on (SSO) to verify users’ identities. MFA requires users to enter a password and a second form of authentication, such as a fingerprint or one-time code, to access their accounts. SSO allows users to access multiple applications using a single set of login credentials, reducing the risk of stolen or weak passwords.There are many Identity Providers like Okta , Azure AD etc which are known for their Identify providing services. Organizations usually do not have to onboard new Identity Providers as Workday provides Identity provisioning Integrations seamlessly integrating data to these providers . Not going into too much detail , here are few screenshots on how to configure SSO with an identity provider in Workday.
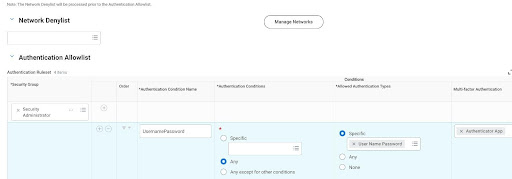
While we discussed how Identity providers check the identity , Workday also provides configuration options in grouping Administrators and providing them different routes to access Workday. A typical example would be to create a backdoor entry for HR Administrators and Security Admins to access Workday using Username and password if the SSO is down due to an issue at the Identity provider. This can be configured using the Manage Authentication Policies task in Workday. This picture gives an idea on configuring access to Security Admins to bypass SSO using Username Password and MFA on Authenticator App.
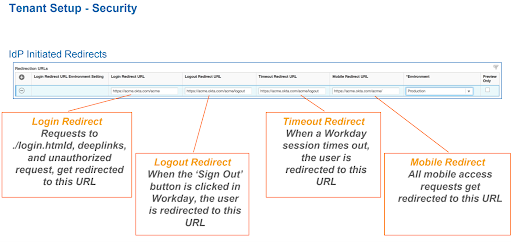
Until now we discussed about Workday integrating to an other Identity provider , However Workday can also be used as a SAML Identity Provider to sign in to other systems via SAML SSO Link. The most common use cases include if you would want your employees to stay in Workday and access links Out side Workday. These external links can be configured as quicklinks on the Business processes , Worklets or even Announcements where you can redirect employees to your company portals.
IP Ranges : Workday also provides us the facility to control (allow or Deny) Access from a particular IP Address or IP Address range. You can control this on the manage authentication policies page for blocking IP Addresses and Maintain IP Range to define IP ranges to access Workday. A Typical Use Can be allowing access for Admins into Workday only from Organisation’s Virtual Private Network Range.
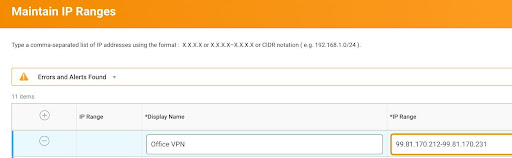
So now that we are aware of different mechanisms an employee can access Workday , the next question that pops up is , but to what data does he have access to? This question is answered in the next section.
2. Role-Based Access Control: Workday’s Role-Based Access Control (RBAC) system assigns users specific roles and permissions based on their job responsibilities. This helps ensure that employees only have access to the data they need to perform their jobs. Diving a bit deep into the technicalities , Workday secures each object with something called a domain. Example : Employee Gender is secured using a domain called Person Data : Gender. Anyone who has access ( View/ Modify) to this domain can see the data that is secured using this domain. This is where experts play around on implementing the best policies of grouping people and defining WHO needs access to WHAT.
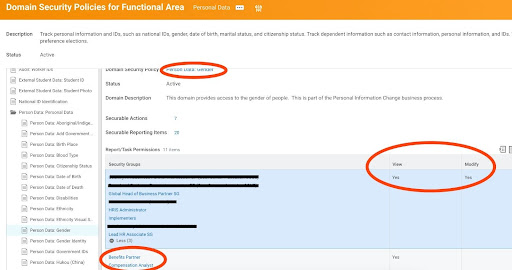
The pic explains how Gender is secured. HRIS Administrator has both View and Modify access while Benefits Partner only has access to View Gender
Grouping options can be configured both static where in a user’s assignment to a group can be driven offline through approvals or it can be sometimes automated based on their geographical location / job profile / organization etc. Here is an example : Workday’s Role based Security provides the flexibility to control access based on the position. A Very simple example could be people from the HR Business Partner Community/group. HR Business partner shall only be able to support employees from his/her location and not from any other location. A HR Business Partner in Sweden cannot and shall not support employees working in Australia. While HR Business Partner is a single group in Workday , Role based security access in Workday allows an admin to configure the support scope based on organizations/locations and also have the flexibility to intersect any such permutations. Roles as seen below can be defined on organizations limiting the access to employee data in only the organizations they support.
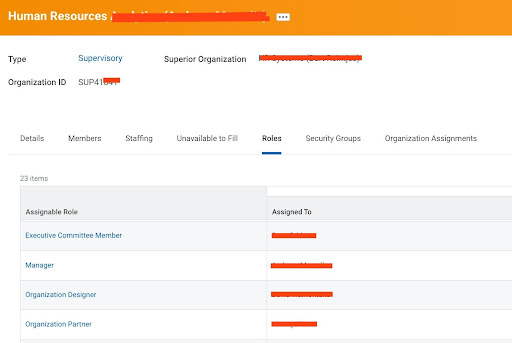
Workday also provides the flexibility to configure user based groups which have global scope. Such a configuration can be used for example to group administrators from recruiting/ talent / benefits etc communities to work on configuration at a global scale and also give the flexibility with employee data at a global level. Such a security group is called a User based security group.One point to consider with such a scenario : An Administrator when leaving the organization shall also be removed from this user based security group and the person coming next into the admin role is not auto assigned to the admin group.
3. Access Restrictions: Some Organizations take one step further in controlling access by restricting access based on the Network Employees are connected to. A typical example is Organisations restricting Managers / HR Advisory to view the Compensation details of their Direct Reports on Mobile outside office Network. Such Restrictions can be configured using the Create Access Restriction Task. Another example would be to restrict Employees/ Managers from downloading attachments outside the Office Network.
4. Scrambling: If you are reading this blog , you may already know Workday’s Tenant Structure. Any Organisation running on Workday would have an implementation tenant , Sandbox , Sandbox Preview and Production. Usually Implementation tenants are the tenants where Most of the Post Production Development takes place. Implementation tenants are refreshed on a periodic/adhoc basis from Production meaning , Implementation tenants where development work is done has production Data. As European Data protection Laws become more strict , Organizations are moving towards scrambling the data in implementation tenants giving their developers no access to production data.Workday’s Inbuilt Scrambling mechanism gives the Administrators the chance to create a plan on what data to be scrambled and when , making it a semi automated process. I call it a semi automated process because there are things which can be improved in terms of scheduling.
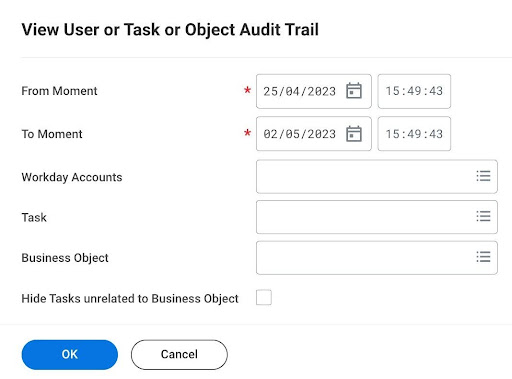
5. Auditing and Monitoring: Workday logs all user activities and provides reports that allow administrators to monitor employee access and detect unauthorized behavior.Many organizations use this report to detect any fraudulent behavior. This report can be exported to create alerts or be given access to third party systems where rule sets could be created . These rule sets can be something like giving an alert if an employee opens a page that he/she does not have access to / is not supposed to open. These techniques will help the system controls in place and will also keep the Risk and Control teams happy for any audits.
6. Compliance: Workday is designed to comply with a range of security and privacy regulations, including GDPR, HIPAA, and SOC 2. The platform undergoes regular audits to ensure compliance with these standards. To ensure the security of employee data in Workday, businesses should follow these best practices:
- Strong Password Policies: Companies should implement strong password policies, including password complexity requirements, password expiration periods, and password history restrictions. They should also encourage employees to use strong passwords and to avoid reusing the same password across multiple accounts
- Access Controls: Administrators should limit employee access to sensitive data and systems. They should also review and update user roles and permissions regularly.
- Employee Training: Companies should provide regular training to employees on cybersecurity best practices, including how to recognize and report phishing attacks and other security threats.
- Regular Auditing and Monitoring: Companies should monitor user activity and review audit logs regularly to identify and respond to suspicious behavior.
- Vendor Management: Companies should vet third-party vendors and service providers carefully to ensure that they meet appropriate security and privacy standards. They should also monitor vendor activities and access to ensure that they comply with company policies.
Conclusion
In conclusion, Workday provides a range of security features to safeguard employee data. However, businesses must take steps to ensure that these features are used effectively, and employees are aware of their responsibilities to maintain data security. By following these best practices, companies can minimize the risk of data breaches and protect their employees’ sensitive data.

